‘Tis the season for phishing. How to recognize, avoid, and report phishing attacks.
It’s that time of year. Cybersecurity attacks typically increase over the holidays and weekends, especially phishing attacks. As an IT MSP we can attest to that from our own experience. We’ve seen a noticeable increase in phishing attacks recently among our clients.
Why? The holidays bring a combination of circumstances that make attacks ideal for cybercriminals.
During the year-end holidays, employees tend to be focused on finishing tasks for the year, cleaning up their agendas, generating end-of-year reports, and so on. Email traffic increases with year-end promotions and last ditch sales efforts. Personal and company email traffic may get mingled as gift-giving and holiday plan-making activities increase. People may not be paying as much attention to their routine email traffic as they might usually be paying. Additionally, security alerts may not receive the notice and attention they usually do.
Also, during the holidays, many employees may be out of the office, or on vacation, staffs may be leaner, and tasks may be temporarily transferred to others less familiar with the usual routines. Hours may be shortened and people who might normally be sought out for approvals or advice may not be easily available.
In short, it’s a good time to get away with a phishing attack.
What is a phishing email?
Your first line of defense is to recognize a phishing email when you get one and to not fall for their tricks.
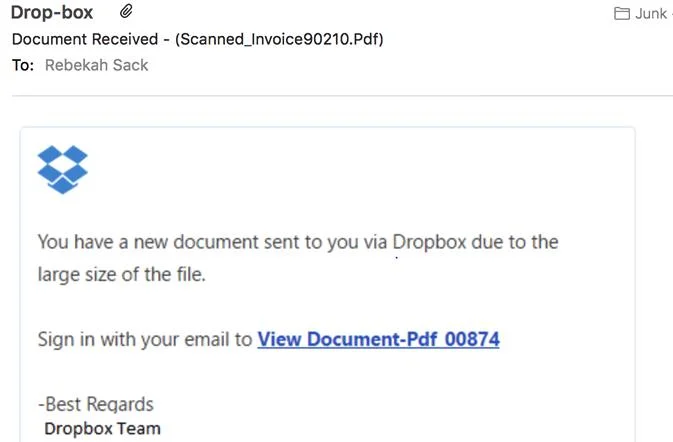
Phishing is when you receive an email or text message that, on the surface looks innocent, but is actually designed to steal information from you. They often look like a legitimate communication you’d ordinarily get from a recognizable organization. The company is familiar, the logo is there, the format looks familiar, but the email is counterfeit.
A phishing email typically tells you there is some problem that needs your attention and asks you to click on a link to help solve the problem. Once you’re transferred to the new destination, you’re asked to put in your credentials, change your information, reveal financial details, etc. At this point, the attacker has the information it needs to dig deeper into your systems and information, send out emails using your account, make financial transactions, download viruses or ransomware, and more.
Typical phishing email approaches to be aware of
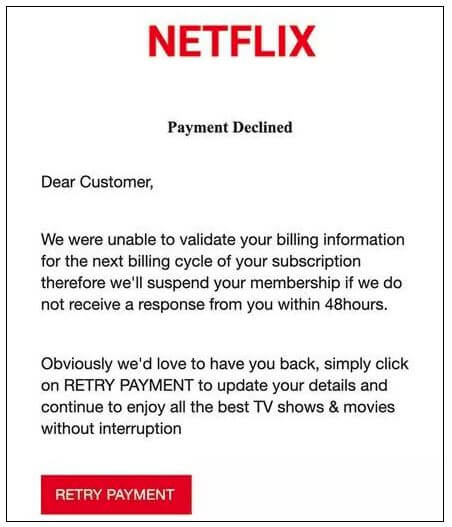
- Email from a “Service” (Netflix, Comcast, etc.) – We’re having trouble processing your latest payment and have placed your account on temporary hold. Some of your billing information appears to be outdated. Please update your information so that we can keep your account current and continue services. Click on the button below to update your account.
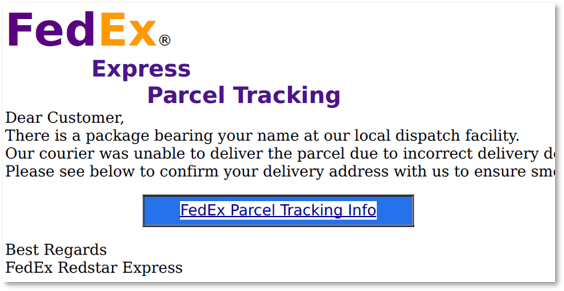
- Email from a “Delivery Service” (UPS. USPS, FedEx, etc.) – Sorry, we were unable to deliver your package. The delivery address and/or other information appears to be incorrect. Please click on the link below to update your account information.
- Email from your “Boss” – Hello, I met earlier with our accounting firm and need you to transfer $5,000 from our regular account to this alternate account in order to deal with a pressing tax issue that has come up. Please do this at your earliest convenience. I’ll paste the link below. I will check in with you later after the transaction is made. Thank you and apologies for the short notice.

- Email from a “Client” – We’ve included you on the distribution list for a recent update we needed to make to one of our contracts. Please review and let us know your thoughts. DocuSign link is below.
- Email from a “Customer” – We are trying to make a payment on our outstanding invoice, and it doesn’t seem to be going through. Could you verify your bank information so that I can make sure we have the right, most current info. Thanks. I really appreciate. The link is provided below.
- Email from a “Friend” – Found these pictures of you I thought you might like. They’re pretty funny. (Link is provided).
- Email from “Social Media” – You’ve received a friend request from _________. Click here to review, accept, or deny.
- Email from a “Benefactor” – Congratulations. As a valued customer you’ve been selected to receive a bonus prize in addition to your usual subscription. Find out how you can take advantage of this limited offer. Button with link included.

In each case you might wonder why you’ve gotten this email. It might seem okay, but you’re not quite sure. If you’re busy you might not think twice and just click on a button to get rid of it. You might have lingering questions or doubts. Maybe it is legit? The normal thing to do would be to click on the link to see if you could get more information that would help you decide.
If you are suspicious at all, don’t click on the link. If you do, don’t provide any further information.
How can you tell phishing emails from your normal email traffic? We all get emails with links and attachments from our co-workers and clients all day long. Which ones are the fake ones?
How to identify a phishing email
- First and foremost, look at the context. Legitimate business emails are usually part of known conversations with people you know. A phishing email most always seems strange and out of place. It deals with a subject you’re not currently working on from a person you can’t quite identify, that doesn’t sound like someone you’ve talked to.
- Legitimate companies for the most part will never email, call, or text you with a link to update information. They will usually encourage you to sign into your account on your own or to call them to review your account details.
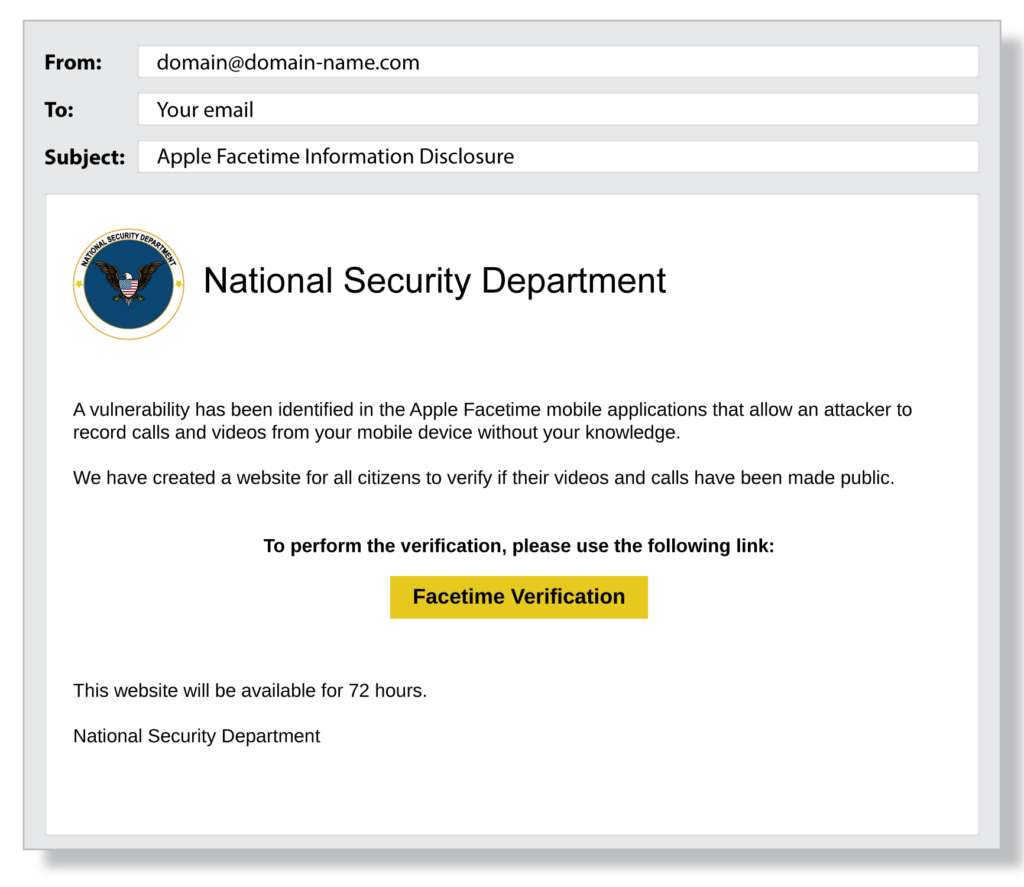
- Check the sender’s full email address. The domain name (the information after the @ symbol) of fake companies is often slightly altered. E.g. instead of deliverytracking@UPS.com it shows as deliverytracking@unitedparcel.com
- Phishing emails often just sound wrong. Pay attention to the spelling and grammar and sound of the email. Typically, phishing emails have several noticeable errors.
- Messages that convey a sense of urgency or distress are often fake. They’re trying to get you to act before you’ve had a chance to think about it.
- URLs, links, and hyperlinked phrases may take you someplace other than what they originally say. The true destination may be hidden. To check, hover your mouse pointer over the link. The true link destination should be visible in a pop up or browser window.
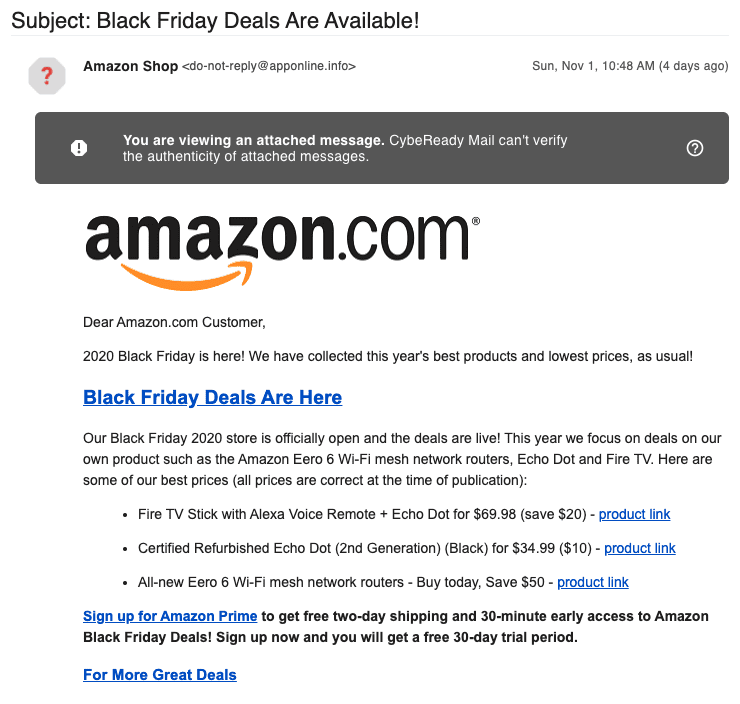
- Anything that needs to be clicked on such as attachments, buttons, links, phrases should always be treated with extreme care.
- Information on contests you didn’t enter, prizes you’ve won, incredible one time deals, are most always suspicious.
How to help protect yourself from phishing attacks
- Make sure your computer is equipped with the proper, updated security software.
- Use Multi-Factor Authentication (MFA) to protect your accounts. MFAs are additional security tools you can use that require you to add another layer of verification when you sign into an account. If they attacker has your name and password, an MFA tool makes it much more difficult to break into your account.
- Use smart passwords and password management tools. Don’t use the same password for multiple accounts.
- Be sure your data is being backed up to an external device or cloud service.

What to do if you think you’ve been phished
- First of all, don’t feel guilty or embarrassed. Clicking on malicious emails or being tricked intro providing information happens to the best of us. We’re all busy or get confused with everything going on and make choices we might not ordinarily make. Sometimes it’s just an accident. Phishers are talented at tricking people. It’s their job.
- If you haven’t already, close the suspicious page or site you’ve been directed to and cut off the communication.
- Report the incident to your manager or IT services provider as soon as possible. Even if you’re not sure and are just suspicious, report the incident as soon as you can. The earlier the situation is addressed the easier it is to successfully remediate.
For more information about guarding agains phishing attacks, contact wedoIT.

